May 11, 2015 Select Allow the connection, then click Next. Choose the profile for which this rule applies, then click Next. Input any name and description, then click Finish. Use the same procedure to open the other ports (138TCP, 138UDP, 139TCP, and 139UDP). Confirm that the port names are added on the Inbound Rules screen, then close Windows Firewall.
Best Firewall For Mac
Although the default setting for your Mac’s firewall should be adequate for most people, you may want to configure your firewall to block additional Internet features for added security. For example, most people will likely need to access e-mail and web pages, but if you never transfer files by using FTP (short for File Transfer Protocol), you can safely block this service.
Don’t configure your firewall unless you’re sure that you know what you’re doing. Otherwise, you may weaken the firewall or lock programs from accessing the Internet and not know how to repair those problems.
Software Firewall To Allow Connection Macbook Pro
To configure your Mac’s firewall, follow these steps:
Choose Command→System Preferences and then click the Security & Privacy icon. Software update mac os x 10.9.
If the lock icon in the lower-left corner of the preferences window is locked, you must unlock it to make changes to your Mac’s user account details. Click the lock icon, type your password in the dialog that appears, and then press Return to unlock your Mac’s user account details.
Click the Firewall tab.
The Firewall preferences pane appears.
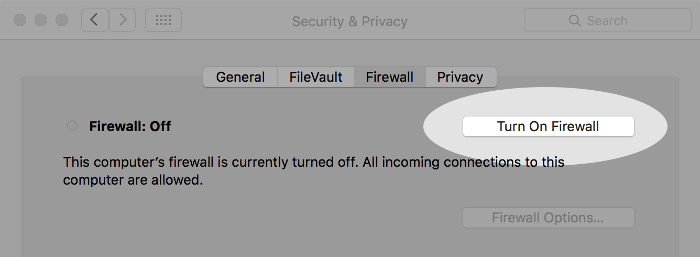
Click the Turn On Firewall button to turn on your Mac’s firewall (if it isn’t already turned on).
Click the Firewall Options button to display the firewall’s custom settings, as shown in this figure.
The dialog that appears offers three check boxes.
In the center list box, you may see one or more sharing services you turned on by using the Sharing preferences pane Command→System Preferences→Sharing).
Select (or deselect) the following check boxes:
Block All Incoming Connections: Allows only essential communications for basic Internet and Mail access; also blocks sharing services, such as iTunes music sharing or Messages screen sharing. When you select this option, any services or applications listed in the pane disappear, replaced with a static warning that indicates all sharing services are being blocked.
Automatically Allow Signed Software to Receive Incoming Connections: Allows typical commercial applications such as Microsoft Word to check for software updates and Safari to access the web.
Enable Stealth Mode: Makes the firewall refuse to respond to any outside attempts to contact it and gather information based on its responses. Cyber monday deals for 2017.
Continue to Step 8 if you want to make additional adjustments to your Mac’s firewall feature; otherwise, skip to Step 13.
(Optional) Click the Add (+) button to add applications that you want to allow or block from communicating over the Internet.
A dialog appears, listing the contents of the Applications folder.
Click a program that you want to allow to access the Internet, such as Dropbox or Skype.
Click Add.
Your chosen program appears under the Applications category.
(Optional) Click the pop-up button to the right of an application in the applications list and choose Allow Incoming Communications or Block Incoming Communications.
(Optional) To remove a program from the applications list, click the program name to select it and click the Delete (–) button below the program list.
Click OK.
Mac Os Firewall Settings
Beginning with Mac OS X 10.7 Lion, your Mac’s security was enhanced with two features:
Advanced Space Layout Randomization (ASLR): Makes your applications more resistant to malicious attacks
Sandboxing: Limits the types of operations an application can do, thereby making it difficult for a threat to take advantage of an application and, consequently, affect the whole operating system. Think of it as strengthening a potential weak link.